LogRhythm's Axon platform needed to transform how security analysts interact with threat data and respond to security events. As a lead Designer, I was tasked with reimagining the analyst workflow and researching how to integrate a new system-wide panel architecture that would fundamentally change how analysts work with the platform.
Researching a new architecture
scroll down to view the project
Disclaimer: Due to confidentiality agreements, the materials involved in this project are limited. I'd be glad to walk-through my process in more detail on a call.
My Role
Primary UX Researcher
Team
1 UX Designer (Myself)
1 Project Managers
4 Dev
Research Timeline
4 weeks
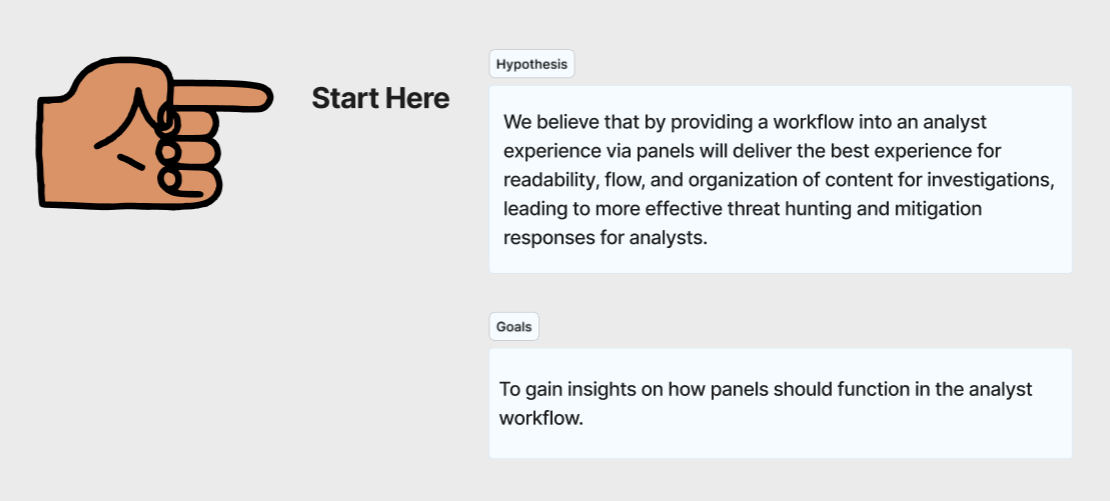
An image of the research hypthesis and goals
This case study illustrates our approach to improving analysis workflows and threat hunting capabilities, while innovating a new UX architectural pattern - a workspace panel drawer that can be accessed throughout the platform.
This research was critical to solving seamless integration with existing platform architecture while addressing multiple panel interactions.
How would you approach a new architecture?
As a UX designer who did not have a designated research team while working on various SaaS features in the cybersecurity sector, I implemented diverse research techniques to validate and inform design decisions around threat detection and analysis workflows. Given the limited availability of security analysts and threat hunters for user testing, maximizing the value of each user interaction was crucial.
Security analysts struggle with disconnected workflows and constant context switching during threat investigations, juggling multiple tabs and windows which led to lost context and reduced efficiency. We needed a solution that would maintain investigation context while allowing analysts to move fluidly through their workflow within existing technical constraints.
Core Objectives
-
Research an intuitive panel-based architecture that supports natural investigation patterns
-
Maintain context and critical information visibility across the platform
-
Create a scalable solution within existing technical constraints that could evolve with analyst needs
Project Stakeholders
Internal
-
Security Analysts
-
Product & Engineering Teams
-
Technical Architecture
External
-
Security Analysts
-
SOC Managers
-
Platform Administrators
-
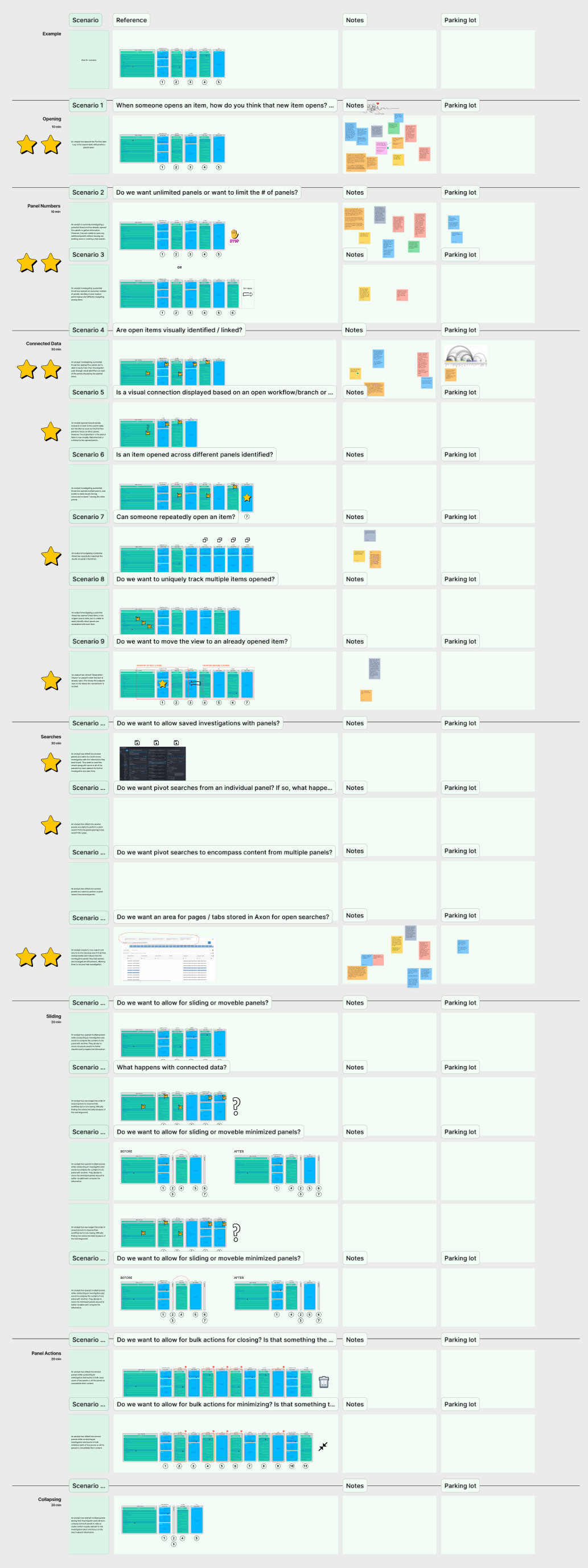
This image shows mapping of architectural questions, scenarios, and behaviors for panels
What I noticed
-
Analysts faced challenges maintaining context when switching between different platform areas during investigations
-
Users needed a way to manage multiple concurrent investigations effectively but lacked proper tools to do so
-
The existing architecture wasn't fully supporting the complex workflow patterns required for threat hunting which panels could solve
-
Critical information needed to remain visible throughout investigations but was difficult to maintain across platform sections
What LogRhythm needed
-
A persistent workspace that could follow analysts throughout their investigation process
-
Better state management capabilities to support complex investigation workflows
-
A more flexible panel system that could maintain context across different areas of the platform
-
Integration of persistent widgets that could work across different panel types
-
A way to enable real-time editing and tracking of changes within investigation panels
User-Centered Approach
Research & Discovery Process
Working on complex security software taught me that effective solutions emerge from deep understanding of analyst workflows combined with technical feasibility. I approached this project with careful attention to both user needs and system constraints.
Initial Research Planning
I was tasked with evaluating and answer questions about a panel-based architecture approach to better support analysis workflows and threat hunting. The core research objectives focused on:
-
Understanding how analysts naturally interact with and utilize the existing panel architecture through direct observation and feedback
-
Mapping technical constraints and opportunities within our current system through collaboration with engineering
-
Identifying optimal approaches to segment features within a panel architecture that aligned with analyst mental models

A diagramatic concept of typical workflows for cybersecurity analysts
This visualization is the general concept for which I was set out to validate the hypothesis that a structured panel-based approach could maintain the benefits of organic discovery while introducing organization and intentionality to the investigation process. The contrast between the chaotic traditional workflow and our proposed panel architecture clearly demonstrated the potential for significant improvement in analyst efficiency and context retention.

This is a view of analyst investigative workflow and panel architecture implementation
Research Methodology
In-depth User Interviews
-
Conducted 5 in-person and 12 remote interviews with both internal and external users
-
Focused on understanding natural investigation workflows and pain points
-
Asked probing questions about context maintenance and multi-investigation management
Sample interview questions:
Can you walk me through your typical investigation workflow?
How do you currently maintain context when switching between different areas of the platform?
What information needs to stay visible throughout your investigation process?
How do you manage multiple concurrent investigations?
Targeted User Surveys & Tests
-
Deployed surveys at strategic points during development
-
Gathered quantitative data on workflow patterns and feature preferences
-
Used multiple choice, A/B testing, usability testing, and free text questions to capture diverse feedback Tools: Sprig, Dovetail, Userlytics
Sample survey questions:
How do you currently manage multiple concurrent investigations? (multiple choice with "Other" option)
What information do you need to maintain while moving between different areas of the platform? (multiple choice with "Other" option)
How helpful would it be to have a workspace that follows you throughout the platform? (Likert scale)
What challenges do you face when trying to maintain context during investigations? (Free text input)
Technical Analysis
-
Collaborated closely with engineering and product teams
-
Created comprehensive scenarios documentation
-
Evaluated architectural limitations and possibilities
-
Recorded all findings from user interviews and surveys into Dovetail and created several detailed reports to inform product direction
The combination of qualitative interviews, quantitative surveys, and technical analysis provided a robust foundation for understanding both user needs and implementation constraints. This multi-faceted approach proved particularly valuable given the limited availability of security analysts for testing.
Research Impacts & Outcomes
Through extensive research involving 5 in-person interviews, 12 remote interviews, and over 40 survey responses, we uncovered crucial insights that shaped our platform's evolution. Using Dovetail for analysis, I identified and categorized key patterns into three comprehensive research reports, ultimately highlighting 50+ potential UX improvements.
46 improvements to Axon Platform
Revolutionary new architecture
Detailed research reports made
Identitfied opportunities for UX enhancement
During this process, I learned that effective security UX design isn't just about creating interfaces – it's about understanding deeply technical workflows and translating them into intuitive experiences that enhance security operations. The workspace panel drawer stands as testament to how thoughtful design can simplify complexity while maintaining the power and flexibility security analysts need.
Lasting Impact
The success of this project demonstrated how thorough research and cross-functional collaboration can transform complex security workflows into intuitive solutions. Despite periods of uncertainty and project pauses, our persistence led to a workspace panel architecture that fundamentally improved how analysts conduct investigations.
What made this project particularly impactful was our ability to balance multiple competing needs:
-
Technical feasibility within existing architecture
-
Analyst workflow requirements
-
Quality assurance considerations
-
Engineering implementation constraints
Want to see more?
I am happy to talk through my research and design work for LogRhythm during a scheduled call, as this work is confidential and cannot be showcased publicly.